


The annual SECUREVAL challenge meeting, part of the PEPR Cybersecurity program led by Patricia Mouy and Sébastien Bardin, was held on Friday, April 4 at CEA-List (NanoInnov).
It brought together key players in security certification — including CESTI teams (Thales, LETI, Serma, Oppida), developers from Thales (DIS, TRT) and SAFRAN, and certifiers from ANSSI (CCN, DST).
The SECUREVAL team shared their latest progress, while guests outlined their current needs and upcoming challenges. The discussions confirmed the strong alignment between SECUREVAL’s work and real-world expectations.The fourth plenary meeting of the SecurEval project was held on 18th September at Nano-Innov, in the CEA-List offices.

We’re proud to share a new article co-written by the SecurEval project leaders, focusing on the Cyber Resilience Act (CRA). The article explores the latest regulatory framework and its impact on digital security and system evaluation. Discover how the CRA shapes the future of cybersecurity and reinforces digital resilience and how the SecurEval project can help.

The third plenary meeting also took place at Campus Cyber, where we presented the project’s work to key players in certification — from ANSSI’s national certification center (CCN) to evaluation labs (CESTI/ITSEF as Serma, CEA-Leti) and developers focused on security vertification ( Thales).

On September 18 and 19, 2023, we held a two-day plenary meeting at Campus Cyber to share the latest progress on the project, with ANSSI joining us.
The event featured great discussions and some really impressive results. It was a fantastic opportunity to connect and move the project forward!
Best poster award was received at GDR GPL 2023 for works on incremental safety analysis with CEA and Sorbonne Université.
Matthéo Vergnolles was awarded for his research internship at CEA for his work on relational analysis and hidden channels.
The SecurEval project is part of the Systems Security theme of this PEPR and concerns the certification of the security of digital systems. Digital system security certification relies on compliance and vulnerability analyses to provide recognized cybersecurity assurances: it is a fundamental element of digital sovereignty and of the European autonomy strategy. France has built an international leadership in this field, but with the drastic increase in the complexity of attacks and systems to be assessed, it is now essential to support its experts with new scientific and technical tools and techniques, covering both hardware and software certifications.
Within the framework of SecurEval, innovative tools will be designed around new digital technologies in order to verify the absence of hardware and software vulnerabilities, and to carry out the required proof of conformity. These developments will be based on a double approach:
In addition, by exploring new techniques for security certifications, this project will also allow France to remain at the state-of-the-art in terms of evaluation capabilities, by anticipating the evolution of international certification schemes.
In order to deal effectively with modern digital systems, code analysis techniques, originally developed for critical systems, must be rethought to fit the objectives of cybersecurity and scale up to complex systems, which combine dedicated functionalities and third-party libraries. This includes:
Downstream of the evaluation, the proof of conformity and compliance with standards remains a manual and time-consuming process. This priority project will explore methodologies and tools to automate proof of compliance for software systems, including when those systems evolve following a vulnerability testing campaign (e.g., bug bounty).
The aim of the project is to design tools based on new digital technologies in order to verify the absence of hardware and software vulnerabilities, and to provide the required proof of conformity. These innovative developments rely on a dual approach:
By exploring new safety certification techniques, this project will enable France to maintain its world-leading capabilities, by anticipating changes in international certification schemes.
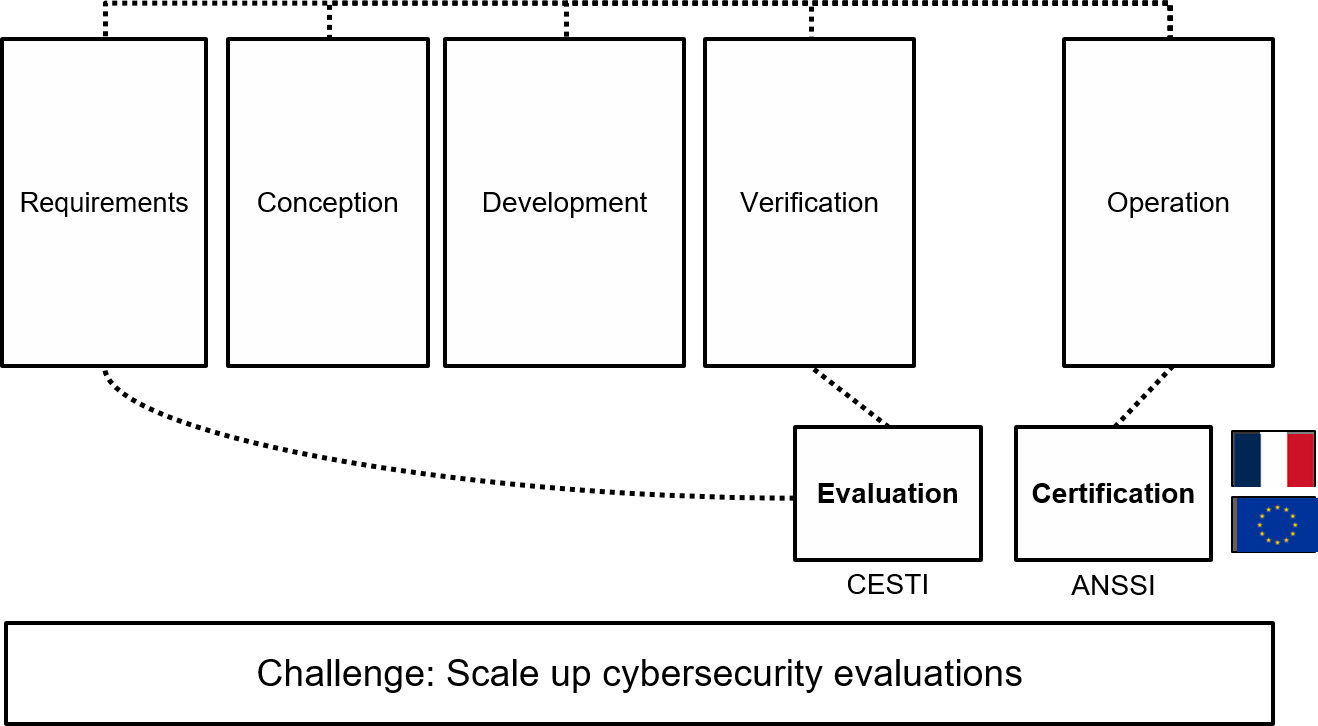
To effectively address the challenges of modern digital systems, traditional code analysis techniques, originally from critical systems, must be revamped to suit security assessment objectives and scale to complex systems combining dedicated functionalities and third-party libraries. This includes:
Downstream of the evaluation, the proof of conformity and compliance with standards remains a manual and time-consuming stage. This priority project aims to develop methodologies and tools that can provide automated compliance verification for software systems, including those that evolve in response to vulnerability testing campaigns (e.g., bug bounty).
The project will place special emphasis on the impact of its results on cybersecurity evaluation professions. The involvement of CESTI CEA teams, particularly during the needs analysis and benchmarking phases, represents a key differentiator of this initiative.